You can read my Enterprise Linux 6.3 to 6.4 risk report on the Red Hat Security Blog.
"for all packages, from release of 6.3 up to and including 6.4, we shipped 108 advisories to address 311 vulnerabilities. 18 advisories were rated critical, 28 were important, and the remaining 62 were moderate and low."
"Updates to correct 77 of the 78 critical vulnerabilities were available via Red Hat Network either the same day or the next calendar day after the issues were public. The other one was in OpenJDK 1.60 where the update took 4 calendar days (over a weekend)."
And if you are interested in how the figures were calculated, here is the working out:
Note that we can't just use a date range because we've pushed some RHSA the weeks before 6.4 that were not included in the 6.4 spin. These issues will get included when we do the 6.4 to 6.5 report (as anyone installing 6.4 will have got them when they first updated).
So just after 6.4 before anything else was pushed that day:
** Product: Red Hat Enterprise Linux 6 server (all packages) ** Dates: 20101110 - 20130221 (835 days) ** 397 advisories (C=55 I=109 L=47 M=186 ) ** 1151 vulnerabilities (C=198 I=185 L=279 M=489 ) ** Product: Red Hat Enterprise Linux 6 Server (default installation packages) ** Dates: 20101110 - 20130221 (835 days) ** 177 advisories (C=11 I=71 L=19 M=76 ) ** 579 vulnerabilities (C=35 I=133 L=159 M=252 )And we need to exclude errata released before 2013-02-21 but not in 6.4:
RHSA-2013:0273 [critical, default] RHSA-2013:0275 [important, not default] RHSA-2013:0272 [critical, not default] RHSA-2013:0271 [critical, not default] RHSA-2013:0270 [moderate, not default] RHSA-2013:0269 [moderate, not default] RHSA-2013:0250 [moderate, default] RHSA-2013:0247 [important, not default] RHSA-2013:0245 [critical, default] RHSA-2013:0219 [moderate, default] RHSA-2013:0216 [important, default] Default vulns from above: critical:12 important:2 moderate:16 low:3 Non-Default vulns from above: critical:4 important:2 moderate:5 low:0This gives us "Fixed between GA and 6.4 iso":
** Product: Red Hat Enterprise Linux 6 server (all packages) ** Dates: 20101110 - 20130221 (835 days) ** 386 advisories (C=51 I=106 L=47 M=182 ) ** 1107 vulnerabilities (C=182 I=181 L=276 M=468 ) ** Product: Red Hat Enterprise Linux 6 Server (default installation packages) ** Dates: 20101110 - 20130221 (835 days) ** 172 advisories (C=9 I=70 L=19 M=74 ) ** 546 vulnerabilities (C=23 I=131 L=156 M=236 )And taken from the last report "Fixed between GA and 6.3 iso":
** Product: Red Hat Enterprise Linux 6 server (all packages) ** Dates: 20101110 - 20120620 (589 days) ** 278 advisories (C=33 I=78 L=31 M=136 ) ** 796 vulnerabilities (C=104 I=140 L=196 M=356 ) ** Product: Red Hat Enterprise Linux 6 Server (default installation packages) ** Dates: 20101110 - 20120620 (589 days) ** 134 advisories (C=6 I=56 L=15 M=57 ) ** 438 vulnerabilities (C=16 I=110 L=126 M=186 )Therefore between 6.3 iso and 6.4 iso:
** Product: Red Hat Enterprise Linux 6 server (all packages) ** Dates: 20120621 - 20130221 (246 days) ** 108 advisories (C=18 I=28 L=16 M=46 ) ** 311 vulnerabilities (C=78 I=41 L=80 M=112 ) ** Product: Red Hat Enterprise Linux 6 Server (default installation packages) ** Dates: 20120621 - 20130221 (246 days) ** 38 advisories (C=3 I=14 L=4 M=17 ) ** 108 vulnerabilities (C=7 I=21 L=30 M=50 )Note: although we have 3 default criticals, they are in openjdk-1.6.0, but we only call Java issues critical if they can be exploited via a browser, and in RHEL6 the Java browser plugin is in the icedtea-web package, which isn't a default package. So that means on a default install you don't get Java plugins running in your browser, so really these are not default criticals in RHEL6 default at all.
You can read my Enterprise Linux 6.2 to 6.3 risk report on the Red Hat Security Blog.
"for all packages, from release of 6.2 up to and including 6.3, we shipped 88 advisories to address 233 vulnerabilities. 15 advisories were rated critical, 23 were important, and the remaining 50 were moderate and low."And if you are interested in how the figures were calculated, as always view the source of this blog entry."Updates to correct 34 of the 36 critical vulnerabilities were available via Red Hat Network either the same day or the next calendar day after the issues were public. The Kerberos telnet flaw was fixed in 2 calendar days as the issue was published on Christmas day. The second PHP flaw took 4 calendar days (over a weekend) as the initial fix released upstream was incomplete."
Red Hat Enterprise Linux 6.2 was released this week (Dec 2011), just over six months since the release of 6.1 in May 2011. So let's use this opportunity to take a quick look back over the vulnerabilities and security updates made in that time, specifically for Red Hat Enterprise Linux 6 Server.
Errata count
The chart below illustrates the total number of security updates issued for Red Hat Enterprise Linux 6 Server if you had installed 6.1, up to and including the 6.2 release, broken down by severity. It's split into two columns, one for the packages you'd get if you did a default install, and the other if you installed every single package (which is unlikely as it would involve a bit of manual effort to select every one). For a given installation, the number of package updates and vulnerabilities that affected you will depend on exactly what you have installed or removed.
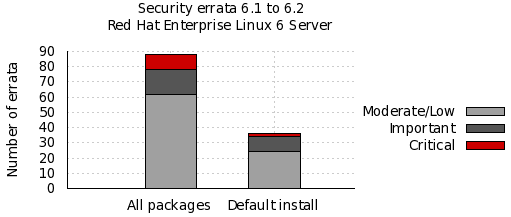
So, for a default install, from release of 6.1 up to and including 6.2, we shipped 36 advisories to address 121 vulnerabilities. 2 advisories were rated critical, 10 were important, and the remaining 24 were moderate and low.
Or, for all packages, from release of 6.1 up to and including 6.2, we shipped 88 advisories to address 218 vulnerabilities. 10 advisories were rated critical, 16 were important, and the remaining 62 were moderate and low.
Critical vulnerabilities
The 10 critical advisories addressed 31 critical vulnerabilities across 3 components:
- Two updates to the OpenJDK 6 Java Runtime (June 2011, October 2011) where a malicious web site presenting a Java applet could potentially run arbitrary code as the user running a web browser.
- Four updates to Firefox (June 2011, August 2011, September 2011, November 2011) where a malicious web site could potentially run arbitrary code as the user running Firefox.
- Four updates to Thunderbird (June 2011, August 2011, September 2011 November 2011) where a malicious email message could potentially run arbitrary code as the user running Thunderbird.
Updates to correct all of the 31 critical vulnerabilities were available via Red Hat Network either the same day or the next calendar day after the issues were public.
Other significant vulnerabilities
Although not in the definition of critical severity, also of interest during this period were a few flaws that were high risk or easily exploitable:
A flaw in Bind, CVE-2011-4313 fixed by RHSA-2011:1458 where a malicious client could cause Bind to stop responding, a denial of service attack. This flaw was discovered by it being accidentally triggered in the wild.
A flaw in the Apache HTTP Server, CVE-2011-3192, fixed by RHSA-2011:1245, where a remote attacker could cause a denial of service attack. This was discovered due to a public exploit.
A flaw in RPM, CVE-2011-3378 fixed by RHSA-2011:1349 where a specially-crafted RPM package that, when queried or installed, would cause rpm to crash or, potentially, execute arbitrary code prior to any signature checking. We're not aware of any working exploits for this issue.
Updates to blacklist the DigiNotar Certificate Authority.
Previous update releases
To compare these statistics with previous update releases we need to take into account that the time between each update release is different. So looking at a default installation and calculating the number of advisories per month gives the following chart:
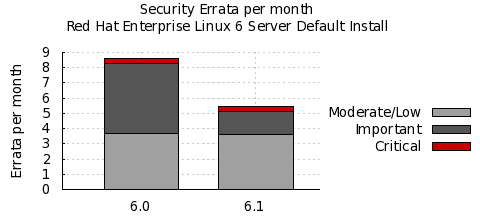
This data is interesting to get a feel for the risk of running Enterprise Linux 6 Server, but isn't really useful for comparisons with other major versions, distributions, or operating systems -- for example, a default install of either Red Hat Enterprise Linux 4AS and 6 Server does not include Firefox, but a default install of 5 Server does. You can use our public security measurement data and tools, and run your own custom metrics for any given Red Hat product, package set, timescales, and severity range of interest.
Red Hat Enterprise Linux 6.1 was released this week (May 2011), just over six months since the release of 6.0 in October 2010. So let's use this opportunity to take a quick look back over the vulnerabilities and security updates made in that time, specifically for Red Hat Enterprise Linux 6 Server.
Errata count
The chart below illustrates the total number of security updates issued for Red Hat Enterprise Linux 6 Server if you had installed 6.0, up to and including the 6.1 release, broken down by severity. It's split into two columns, one for the packages you'd get if you did a default install, and the other if you installed every single package (which is unlikely as it would involve a bit of manual effort to select every one). For a given installation, the number of package updates and vulnerabilities that affected you will depend on exactly what you have installed or removed.
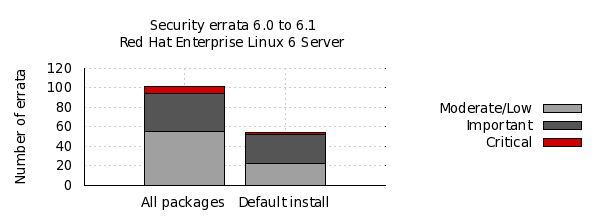
So, for a default install, from release of 6.0 up to and including 6.1, we shipped 54 advisories to address 195 vulnerabilities. 2 advisories were rated critical, 29 were important, and the remaining 23 were moderate and low.
Or, for all packages, from release of 6.0 up to and including 6.1, we shipped 102 advisories to address 345 vulnerabilities. 8 advisories were rated critical, 39 were important, and the remaining 55 were moderate and low.
These figures include 10 advisories we released on the day we shipped 6.0. This was because we froze package updates some months before releasing the product. Two of those updates were rated critical, an update to Firefox, and to Samba.
Critical vulnerabilities
The 8 critical advisories addressed 37 critical vulnerabilities across 4 components:
- An update to Samba (October 2010) where a malicious client could potentially run arbitrary code as the Samba server. Samba is a default install package but the server is not enabled by default.
- Four updates to Firefox (October 2010, December 2010, March 2011, April 2011) where a malicious web site could potentially run arbitrary code as the user running Firefox.
- Two updates to Thunderbird (March 2011, April 2011) where a malicious email message could potentially run arbitrary code as the user running Thunderbird.
- An update to Pango (March 2011) where an application using Pango to parse untrusted font data (such as Firefox) could potentially run arbitrary code as the privileges of the user. Pango is a default install package.
Updates to correct all of the 37 critical vulnerabilities were available via Red Hat Network either the same day or the next calendar day after the issues were public.
This data is interesting to get a feel for the risk of running Enterprise Linux 6 Server, but isn't really useful for comparisons with other major versions, distributions, or operating systems -- for example, a default install of Red Hat Enterprise Linux 4AS and 6 Server did not include Firefox, but 5 Server does. You can use our public security measurement data and tools, and run your own custom metrics for any given Red Hat product, package set, timescales, and severity range of interest.
