Red Hat Enterprise Linux 5.7 was released last week (July 2011), six months since the release of 5.6 in January 2011. So let's use this opportunity to take a quick look back over the vulnerabilities and security updates made in that time, specifically for Red Hat Enterprise Linux 5 Server.
Errata count
The chart below illustrates the total number of security updates issued for Red Hat Enterprise Linux 5 Server if you had installed 5.6, up to and including the 5.7 release, broken down by severity. It's split into two columns, one for the packages you'd get if you did a default install, and the other if you installed every single package (which is unlikely as it would involve quite a bit of manual effort to select every one). For a given installation, the number of package updates and vulnerabilities that affected you will depend on exactly what packages you have installed or removed.
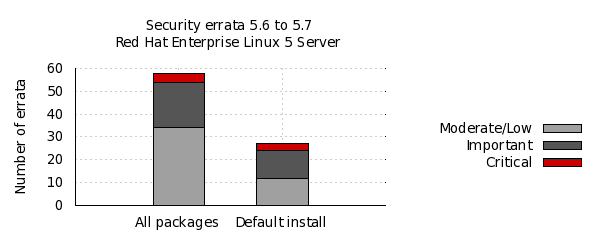
So, for a default install, from release of 5.6 up to and including 5.7, we shipped 27 advisories to address 109 vulnerabilities. 3 advisories were rated critical, 12 were important, and the remaining 12 were moderate and low.
Or, for all packages, from release of 5.6 to and including 5.7, we shipped 58 advisories to address 172 vulnerabilities. 4 advisories were rated critical, 20 were important, and the remaining 34 were moderate and low.
Critical vulnerabilities
The 4 critical advisories addressed 34 critical vulnerabilities across just 2 different packages:
- An update to OpenJDK 6 Java Runtime Environment, (June 2011) where a web site hosting a malicious Java applet could potentially run arbitrary code as the user.
- Three updates to Firefox (March 2011, April 2011, June 2011) where a malicious web site could potentially run arbitrary code as the user running Firefox.
Updates to correct all of the 34 critical vulnerabilities were available via Red Hat Network either the same day or the next calendar day after the issues were public.
Overall, for Red Hat Enterprise Linux 5 since release until 5.7, 97% of critical vulnerabilities have had an update available to address them available from the Red Hat Network either the same day or the next calendar day after the issue was public.
Other significant vulnerabilities
Although not in the definition of critical severity, also of interest during this period were a couple of flaws that were easily exploitable:
- A flaw in dhcp, CVE-2011-0997, fixed by RHSA-2011:0428, where a malicious DHCP server could send a response that could lead to arbitrary code execution on connecting clients.
- A flaw in glibc, CVE-2011-0536, fixed by RHSA-2011:0412, where a local user could gain root privileges.
In addition, updates to Firefox and NSS were made to blacklist a number of compromised SSL certificates.
Previous update releases
To compare these statistics with previous update releases we need to take into account that the time between each update release is different. So looking at a default installation and calculating the number of advisories per month gives the following chart:
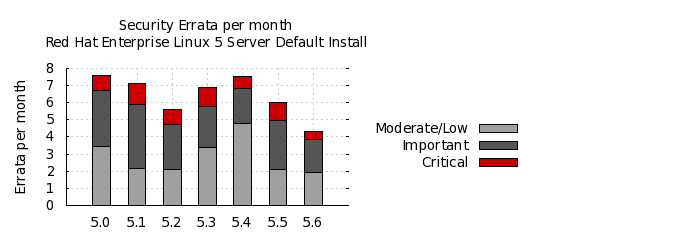
This data is interesting to get a feel for the risk of running Enterprise Linux 5 Server, but isn't really useful for comparisons with other major versions, distributions, or operating systems -- for example, a default install of Red Hat Enterprise Linux 4AS did not include Firefox, but 5 Server does. You can use our public security measurement data and tools, and run your own custom metrics for any given Red Hat product, package set, timescales, and severity range of interest.
See also: 5.5 to 5.6, 5.4 to 5.5, 5.3 to 5.4, 5.2 to 5.3, 5.1 to 5.2, and 5.0 to 5.1 risk reports.
Red Hat Enterprise Linux 6.1 was released this week (May 2011), just over six months since the release of 6.0 in October 2010. So let's use this opportunity to take a quick look back over the vulnerabilities and security updates made in that time, specifically for Red Hat Enterprise Linux 6 Server.
Errata count
The chart below illustrates the total number of security updates issued for Red Hat Enterprise Linux 6 Server if you had installed 6.0, up to and including the 6.1 release, broken down by severity. It's split into two columns, one for the packages you'd get if you did a default install, and the other if you installed every single package (which is unlikely as it would involve a bit of manual effort to select every one). For a given installation, the number of package updates and vulnerabilities that affected you will depend on exactly what you have installed or removed.
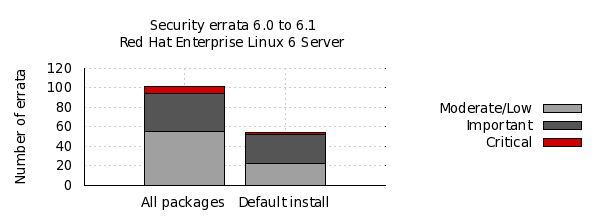
So, for a default install, from release of 6.0 up to and including 6.1, we shipped 54 advisories to address 195 vulnerabilities. 2 advisories were rated critical, 29 were important, and the remaining 23 were moderate and low.
Or, for all packages, from release of 6.0 up to and including 6.1, we shipped 102 advisories to address 345 vulnerabilities. 8 advisories were rated critical, 39 were important, and the remaining 55 were moderate and low.
These figures include 10 advisories we released on the day we shipped 6.0. This was because we froze package updates some months before releasing the product. Two of those updates were rated critical, an update to Firefox, and to Samba.
Critical vulnerabilities
The 8 critical advisories addressed 37 critical vulnerabilities across 4 components:
- An update to Samba (October 2010) where a malicious client could potentially run arbitrary code as the Samba server. Samba is a default install package but the server is not enabled by default.
- Four updates to Firefox (October 2010, December 2010, March 2011, April 2011) where a malicious web site could potentially run arbitrary code as the user running Firefox.
- Two updates to Thunderbird (March 2011, April 2011) where a malicious email message could potentially run arbitrary code as the user running Thunderbird.
- An update to Pango (March 2011) where an application using Pango to parse untrusted font data (such as Firefox) could potentially run arbitrary code as the privileges of the user. Pango is a default install package.
Updates to correct all of the 37 critical vulnerabilities were available via Red Hat Network either the same day or the next calendar day after the issues were public.
This data is interesting to get a feel for the risk of running Enterprise Linux 6 Server, but isn't really useful for comparisons with other major versions, distributions, or operating systems -- for example, a default install of Red Hat Enterprise Linux 4AS and 6 Server did not include Firefox, but 5 Server does. You can use our public security measurement data and tools, and run your own custom metrics for any given Red Hat product, package set, timescales, and severity range of interest.
Earlier this year, Red Hat joined the Common Vulnerability Reporting Framework (CVRF) working group run by ICASI. The goal of CVRF is to provide a way to share information about security updates in a machine-readable format. Red Hat already produce a version of our security advisories in machine readable format, as OVAL definitions, but these are really designed for automated test tools to determine the need to apply an update. CVRF looked like it would be more useful for providing customers with a machine readable view of our advisories.
After many iterations at getting right schema, CVRF 1.0 was released this week.
Red Hat is not yet providing an official archive with CVRF representations of our advisories, but we have created tools internally to support it and allow us to automatically create CVRF documents based on our advisory database. We've provided a sample set of advisories in CVRF format for download.
Let's take one of these samples, a recent Red Hat Enterprise Linux security advisory and examine how it looks when automatically converted to a CVRF document. Our advisories often fix more than one vulnerability at a time and for more than one version of a product, but for this example we'll keep it simple. RHSA-2010:0888 is an Enterprise Linux 6 update to fix the vulnerability CVE-2010-3864 affecting OpenSSL.
The CVRF for this advisory starts like this:
<?xml version="1.0" encoding="utf-8"?>
<cvrfdoc xmlns="https://www.icasi.org/CVRF/schema/cvrf/1.0"
xmlns:cvrf="https://www.icasi.org/CVRF/schema/cvrf/1.0"
xmlns:cvrf-vuln="https://www.icasi.org/CVRF/schema/vuln/1.0">
<DocumentTitle xml:lang="en">Red Hat Security Advisory: openssl security update</DocumentTitle>
<DocumentDistribution xml:lang="en">Copyright © 2011 Red Hat, Inc. All rights reserved.</DocumentDistribution>
<LegalDisclaimer xml:lang="en">Please see https://www.redhat.com/legal/legal_statement.html</LegalDisclaimer>
<DocumentType>Security Advisory</DocumentType>
<DocumentPublisher>Vendor</DocumentPublisher>
<DocumentTracking>
<DocumentID>RHSA-2010:0888</DocumentID>
<DocumentStatus>Final</DocumentStatus>
<DocumentVersion>1</DocumentVersion>
<DocumentRevisionHistory>
<DocumentRevision>
<RevisionNumber>1.0</RevisionNumber>
<RevisionDate>2010-11-16T16:08:00+00:00</RevisionDate>
<RevisionDescription>Current version</RevisionDescription>
</DocumentRevision>
</DocumentRevisionHistory>
<DocumentInitialReleaseDate>2010-11-16T16:08:00+00:00</DocumentInitialReleaseDate>
<DocumentCurrentReleaseDate>2010-11-16T16:08:00+00:00</DocumentCurrentReleaseDate>
<DocumentGenerator>
<Generator>make-cvrf-from-et.pl</Generator>
<GenerationDate>2010-12-15T10:15:06+00:00</GenerationDate>
<CVRFVersion>1.00</CVRFVersion>
</DocumentGenerator>
</DocumentTracking>
<DocumentSummary>
<Summary Title="Topic" Audience="General" xml:lang="en">
Updated openssl packages that fix one security issue are now available for
Red Hat Enterprise Linux 6.
The Red Hat Security Response Team has rated this update as having
important security impact. A Common Vulnerability Scoring System (CVSS)
base score, which gives a detailed severity rating, is available from the
CVE link in the References section.
</Summary>
</DocumentSummary>
<DocumentDetails>
<Details Title="Details" Audience="General" xml:lang="en">
OpenSSL is a toolkit that implements the Secure Sockets Layer (SSL v2/v3)
and Transport Layer Security (TLS v1) protocols, as well as a
full-strength, general purpose cryptography library.
A race condition flaw has been found in the OpenSSL TLS server extension
parsing code, which could affect some multithreaded OpenSSL applications.
Under certain specific conditions, it may be possible for a remote attacker
to trigger this race condition and cause such an application to crash, or
possibly execute arbitrary code with the permissions of the application.
(CVE-2010-3864)
Note that this issue does not affect the Apache HTTP Server. Refer to Red
Hat Bugzilla bug 649304 for more technical details on how to determine if
your application is affected.
Red Hat would like to thank Rob Hulswit for reporting this issue.
All OpenSSL users should upgrade to these updated packages, which contain a
backported patch to resolve this issue. For the update to take effect, all
services linked to the OpenSSL library must be restarted, or the system
rebooted.
</Details>
</DocumentDetails>
<References>
<RelatedDocument>
<DocumentURL>https://rhn.redhat.com/errata/RHSA-2010-0888.html</DocumentURL>
<DocumentDescription>https://rhn.redhat.com/errata/RHSA-2010-0888.html</DocumentDescription>
</RelatedDocument>
<RelatedDocument>
<DocumentURL>https://www.redhat.com/security/updates/classification/#important</DocumentURL>
<DocumentDescription>https://www.redhat.com/security/updates/classification/#important</DocumentDescription>
</RelatedDocument>
</References>
The final top level directives give our severity rating and issuing authority. The severity is a free-text field and it's up to each vendor to use their own scheme for this. In the earlier references section we already gave a URL that described the severity levels being used; for a future CVRF version we should have that URL referenced as part of the AggregateSeverity tag.<AggregateSeverity>Important</AggregateSeverity> <IssuingAuthority VendorID="Red Hat, Inc">secalert@redhat.com</IssuingAuthority>
<cvrf-vuln:Vulnerability>
<cvrf-vuln:VulnerabilityID><cvrf-vuln:Value SystemName="CVE">CVE-2010-3864</cvrf-vuln:Value></cvrf-vuln:VulnerabilityID>
<cvrf-vuln:VulnerabilityDetails xml:lang="en">A race condition flaw
has been found in the OpenSSL TLS server extension parsing code, which could
affect some multithreaded OpenSSL applications. Under certain specific
conditions, it may be possible for a remote attacker to trigger this race
condition and cause such an application to crash, or possibly execute
arbitrary code with the permissions of the
application. </cvrf-vuln:VulnerabilityDetails>
<cvrf-vuln:VendorRemediationStatus>Completed</cvrf-vuln:VendorRemediationStatus>
<cvrf-vuln:CVE>CVE-2010-3864</cvrf-vuln:CVE>
<cvrf-vuln:Threat><cvrf-vuln:Impact>Important</cvrf-vuln:Impact></cvrf-vuln:Threat>
<cvrf-vuln:ProductFamily>Red Hat Enterprise Linux</cvrf-vuln:ProductFamily>
<cvrf-vuln:Acknowledgment>Red Hat would like to thank Rob Hulswit for reporting this issue.</cvrf-vuln:Acknowledgment>
<cvrf-vuln:CVSS>
<cvrf-vuln:CVSSBaseScore>7.6</cvrf-vuln:CVSSBaseScore>
<cvrf-vuln:CVSSScoringVector>AV:N/AC:H/Au:N/C:C/I:C/A:C</cvrf-vuln:CVSSScoringVector>
</cvrf-vuln:CVSS>
<cvrf-vuln:Remediation>
<cvrf-vuln:VendorFix xml:lang="en">
Before applying this update, make sure all previously-released errata
relevant to your system have been applied.
This update is available via the Red Hat Network. Details on how to
use the Red Hat Network to apply this update are available at
https://kbase.redhat.com/faq/docs/DOC-11259
</cvrf-vuln:VendorFix>
</cvrf-vuln:Remediation>
<cvrf-vuln:AffectedPlatform Name="Red Hat Enterprise Linux">
<cvrf-vuln:AffectedRelease Name="Red Hat Enterprise Linux Desktop Optional (v. 6)">
<cvrf-vuln:Version Type="Fixed">openssl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-debuginfo-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-devel-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-perl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-static-1.0.0-4.el6_0.1</cvrf-vuln:Version>
</cvrf-vuln:AffectedRelease>
<cvrf-vuln:AffectedRelease Name="Red Hat Enterprise Linux HPC Node Optional (v. 6)">
<cvrf-vuln:Version Type="Fixed">openssl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-debuginfo-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-devel-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-perl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-static-1.0.0-4.el6_0.1</cvrf-vuln:Version>
</cvrf-vuln:AffectedRelease>
<cvrf-vuln:AffectedRelease Name="Red Hat Enterprise Linux Workstation Optional (v. 6)">
<cvrf-vuln:Version Type="Fixed">openssl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-debuginfo-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-perl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-static-1.0.0-4.el6_0.1</cvrf-vuln:Version>
</cvrf-vuln:AffectedRelease>
<cvrf-vuln:AffectedRelease Name="Red Hat Enterprise Linux Workstation (v. 6)">
<cvrf-vuln:Version Type="Fixed">openssl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-debuginfo-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-devel-1.0.0-4.el6_0.1</cvrf-vuln:Version>
</cvrf-vuln:AffectedRelease>
<cvrf-vuln:AffectedRelease Name="Red Hat Enterprise Linux HPC Node (v. 6)">
<cvrf-vuln:Version Type="Fixed">openssl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-debuginfo-1.0.0-4.el6_0.1</cvrf-vuln:Version>
</cvrf-vuln:AffectedRelease>
<cvrf-vuln:AffectedRelease Name="Red Hat Enterprise Linux Server Optional (v. 6)">
<cvrf-vuln:Version Type="Fixed">openssl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-debuginfo-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-perl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-static-1.0.0-4.el6_0.1</cvrf-vuln:Version>
</cvrf-vuln:AffectedRelease>
<cvrf-vuln:AffectedRelease Name="Red Hat Enterprise Linux Desktop (v. 6)">
<cvrf-vuln:Version Type="Fixed">openssl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-debuginfo-1.0.0-4.el6_0.1</cvrf-vuln:Version>
</cvrf-vuln:AffectedRelease>
<cvrf-vuln:AffectedRelease Name="Red Hat Enterprise Linux Server (v. 6)">
<cvrf-vuln:Version Type="Fixed">openssl-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-debuginfo-1.0.0-4.el6_0.1</cvrf-vuln:Version>
<cvrf-vuln:Version Type="Fixed">openssl-devel-1.0.0-4.el6_0.1</cvrf-vuln:Version>
</cvrf-vuln:AffectedRelease>
</cvrf-vuln:AffectedPlatform>
<cvrf-vuln:References>
<cvrf-vuln:RelatedDocument>
<cvrf-vuln:DocumentURL>https://www.redhat.com/security/data/cve/CVE-2010-3864.html</cvrf-vuln:DocumentURL>
<cvrf-vuln:DocumentDescription>CVE-2010-3864</cvrf-vuln:DocumentDescription>
</cvrf-vuln:RelatedDocument>
<cvrf-vuln:RelatedDocument>
<cvrf-vuln:DocumentURL>https://bugzilla.redhat.com/show_bug.cgi?id=649304</cvrf-vuln:DocumentURL>
<cvrf-vuln:DocumentDescription>bz#649304: CVE-2010-3864 OpenSSL TLS extension parsing race condition</cvrf-vuln:DocumentDescription>
</cvrf-vuln:RelatedDocument>
</cvrf-vuln:References>
</cvrf-vuln:Vulnerability>
</cvrfdoc>
Our example advisory only had one vulnerability, but the whole vulnerability section is repeated where multiple are addressed.
Overall we've been really pleased with the way CVRF has turned out for it's first release, and we think it will be a useful way for vendors such as us to provide machine-readable advisories to customers as well as to tool vendors, filling a gap between our OVAL XML and our text and HTML advisories. We'll be trialling CVRF advisories later this year, drop an email to secalert@redhat.com if you have comments on our CVRF samples.
Red Hat Enterprise Linux 5.6 was released last week (January 2011), nearly ten months since the release of 5.5 in March 2010. So let's use this opportunity to take a quick look back over the vulnerabilities and security updates made in that time, specifically for Red Hat Enterprise Linux 5 Server.
Errata count
The chart below illustrates the total number of security updates issued for Red Hat Enterprise Linux 5 Server if you had installed 5.5, up to and including the 5.6 release, broken down by severity. It's split into two columns, one for the packages you'd get if you did a default install, and the other if you installed every single package (which is unlikely as it would involve a bit of manual effort to select every one). For a given installation, the number of package updates and vulnerabilities that affected you will depend on exactly what you have installed or removed.
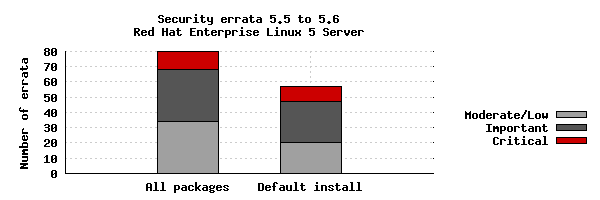
So, for a default install, from release of 5.5 up to and including 5.6, we shipped 57 advisories to address 206 vulnerabilities. 10 advisories were rated critical, 27 were important, and the remaining 20 were moderate and low.
Or, for all packages, from release of 5.5 to and including 5.6, we shipped 80 advisories to address 300 vulnerabilities. 12 advisories were rated critical, 34 were important, and the remaining 34 were moderate and low.
Critical vulnerabilities
The 12 critical advisories addressed 49 critical vulnerabilities across just 3 different packages:
- An update to the Exim Internet Mailer, (December 2010), where an unauthenticated remote attacker could run arbitrary code as root on a server. Exim is not a default package or enabled by default. There is a public exploit for this issue which worked on Red Hat Enterprise Linux 5.
- Two updates over three advisories to Samba, (June 2010 for Samba 3.0 and Samba 3.3, September 2010 for Samba 3.0 and Samba 3.3), where a malicious client could send a specially-crafted SMB packet to the Samba server, potentially resulting in arbitrary code execution with the privileges of the Samba server. I'm not aware of any working public exploits for these issues.
- Eight updates to Firefox (March 2010, June 2010, 20 July 2010, 23 July 2010, September 2010, 19 October 2010, 27 October 2010, December 2010) where a malicious web site could potentially run arbitrary code as the user running Firefox.
Updates to correct 48 out of the 49 critical vulnerabilities were available via Red Hat Network either the same day or the next calendar day after the issues were public. The update to fix Exim took 3 calendar days from the date of the report to the Exim developers.
Overall, for Red Hat Enterprise Linux 5 since release until 5.6, 97% of critical vulnerabilities have had an update available to address them available from the Red Hat Network either the same day or the next calendar day after the issue was public.
Other significant vulnerabilities
Although not in the definition of critical severity, also of interest during this period were several kernel flaws that where an local user could gain root privileges. The following had publicly available exploits:- A fix for CVE-2010-2240 was provided by RHSA-2010-0661 (August 2010). The public exploit did not work against Red Hat Enterprise Linux 5, but it may be possible to create one that does.
- A fix for CVE-2010-3081 was provided by RHSA-2010-0704 (September 2010). The public exploit worked against Red Hat Enterprise Linux 5
- A fix for CVE-2010-3904 was provided by RHSA-2010-0792 (October 2010). The public exploit did not work against Red Hat Enterprise Linux 5 but it is possible to create one that does.
Previous updates
To compare these statistics with previous update releases we need to take into account that the time between each update is different. So looking at a default installation and calculating the number of advisories per month gives the following chart:
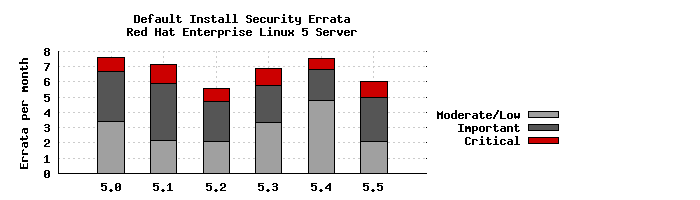
This data is interesting to get a feel for the risk of running Enterprise Linux 5 Server, but isn't really useful for comparisons with other major versions, distributions, or operating systems -- for example, a default install of Red Hat Enterprise Linux 4AS did not include Firefox, but 5 Server does. You can use our public security measurement data and tools, and run your own custom metrics for any given Red Hat product, package set, timescales, and severity range of interest.
See also: 5.4 to 5.5, 5.3 to 5.4, 5.2 to 5.3, 5.1 to 5.2, and 5.0 to 5.1 risk reports.
You have a new email! (ping!)
Hold on a second. It might be important. I'd better go and read it. Oh it's just a note confirming some meeting for next week. Deleted. Now, what was I working on?
A few years ago, when I was analysing where my time was going, (and why I was working 60+ hour weeks), I figured out that the context switching caused by being unable to concentrate on a task for more than a few minutes was a major productivity drain.
It's hard to resist a new email. My new cellphone takes great delight in having 'push' email and would really like to beep on each new message I receive. The web is full of gmail notifier applications designed specifically to interrupt you to some important new mail. Even my favourite command-line email client, Alpine, likes to ping you about new mail arriving in your inbox even if you're busy in some other mailbox or composing a mail.
Alpine ought to have some sort of "don't notify me" option, but in the meantime I apply the brute-force patch below to disable it.
This 5-minute patch has saved me several hours of task switching every week, and although this means it can sometimes be an hour or two between me checking my inbox, no one has really noticed.
--- alpine-2.00/pith/newmail.c.orig 2010-07-19 16:47:01.127480500 +0100
+++ alpine-2.00/pith/newmail.c 2010-07-19 16:47:35.657602347 +0100
@@ -680,7 +680,7 @@
}
format_new_mail_msg(folder, number, e, intro, from, subject, subjtext, sizeof(subject));
-
+#if 0
if(!for_new_mail_win)
q_status_message5(SM_ASYNC | SM_DING, 0, 60,
"%s%s%s%.80s%.80s", intro,
@@ -706,6 +706,7 @@
#endif
}
#endif
+#endif
if(pith_opt_icon_text){
if(F_ON(F_ENABLE_XTERM_NEWMAIL, ps_global)
Two years ago I published a table of Vulnerability and threat mitigation features in Red Hat Enterprise Linux and Fedora. Now that we've released Red Hat Enterprise Linux 6, it's time to update the table. Thanks to Eugene Teo for collating this information.
Between releases there are lots of changes made to improve security and we've not listed everything; just a high-level overview of the things we think are most interesting that help mitigate security risk. We could go into much more detail, breaking out the number of daemons covered by the SELinux default policy, the number of binaries compiled PIE, and so on.
Note that this table is for the most common architectures, x86 and x86_64 only; other supported architectures may vary.
| Features | Red Hat Enterprise Linux | |||
| 3 | 4 | 5 | 6 | |
| 2003 Oct | 2005 Feb | 2007 Mar | 2010 Nov | |
| Firewall by default | Y | Y | Y | Y |
| Signed updates required by default | Y | Y | Y | Y |
| NX emulation using segment limits by default | Y(since 9/2004) | Y | Y | Y |
| Support for Position Independent Executables (PIE) | Y(since 9/2004) | Y | Y | Y |
| Address Randomization (ASLR) for Stack/mmap by default | Y (since 9/2004) | Y | Y | Y |
| ASLR for vDSO (if vDSO enabled) | no vDSO | Y | Y | Y |
| Support for NULL pointer dereference protection | Y(since 11/2009) | Y(since 9/2009) | Y(since 5/2008) | Y |
| NX for supported processors/kernels by default | Y(since 9/2004) | Y | Y | Y |
| Support for block module loading via cap-bound sysctl tunable or /proc/sys/kernel/cap-bound |
Y | Y | Y | no cap-bound |
| Restricted access to kernel memory by default | Y | Y | Y | |
| Support for SELinux | Y | Y | Y | |
| SELinux enabled with targeted policy by default | Y | Y | Y | |
| glibc heap/memory checks by default | Y | Y | Y | |
| Support for FORTIFY_SOURCE, used on selected packages | Y | Y | Y | |
| Support for ELF Data Hardening | Y | Y | Y | |
| All packages compiled using FORTIFY_SOURCE | Y | Y | ||
| All packages compiled with stack smashing protection | Y | Y | ||
| SELinux Executable Memory Protection | Y | Y | ||
| glibc pointer encryption by default | Y | Y | ||
| Enabled NULL pointer dereference protection by default | Y(since 5/2008) | Y | ||
| Enabled write-protection for kernel read-only data structures by default |
Y | Y | ||
| FORTIFY_SOURCE extensions including C++ coverage | Y | |||
| Support for block module loading via modules_disabled sysctl tunable or /proc/sys/kernel/modules_disabled |
Y | |||
| Support for SELinux to restrict the loading of kernel modules by unprivileged processes in confined domains |
Y | |||
| Enabled kernel -fstack-protector buffer overflow detection by default | Y | |||
| Support for sVirt labelling to provide security over guest instances | Y | |||
| Support for SELinux to confine users' access on a system | Y | |||
| Support for SELinux to test untrusted content via a sandbox | Y | |||
| Support for SELinux X Access Control Extension (XACE) | Y | |||
Starting with Red Hat Enterprise Linux 6 we have switched to using SHA-256 signatures on all RPM packages and to a 4096-bit RSA signing key.
We've done this because it is current best practice to migrate away from MD5 and SHA-1 hashes due to various flaws found in them. Those flaws don't yet directly pose a threat to package signing however, and therefore our existing shipped products which used these older hashes will continue to use their existing keys until they reach their end of life.
A similar switch to stronger signing was already made in Fedora 11. This switch involved some changes to the RPM application.
So what this means is that we used new signing keys for both the beta and final release packages for Red Hat Enterprise Linux 6. Those keys were created and are protected by a hardware security module, as we've done with previous keys.
Details and fingerprint of the new key, #fd431d51.
Also in the Red Hat Enterprise Linux 6 distribution we've started
to simplify the layout of the key files in
the /etc/pki/rpm-gpg/
directory:
- RPM-GPG-KEY-redhat-beta : Both the old and new beta keys
- RPM-GPG-KEY-redhat-release : Both the new signing key and the auxiliary key
- RPM-GPG-KEY-redhat-legacy-release : The signing key used for EL5
- RPM-GPG-KEY-redhat-legacy-former : The signing key used for products before EL5
- RPM-GPG-KEY-redhat-legacy-rhx : The signing key used for RHX
The auxiliary key mentioned above is for emergency use. We created it some time ago on a new standalone machine, took a hardcopy printout of the private key and passphrase, stored them separately and securely, and destroyed the software copies. We've planned for many eventualities, but in the unlikely event we lose the ability to sign with the hardware key we could retrieve the printout, type in the key, and continue to sign updates.

For our first wedding aniversary this weekend my lovely wife bought me a new gadget, an Akai MPK-25 midi keyboard. The last Sonik gig that I played at we used full-sized midi keyboards hooked to real synth modules, but for our next gig later this year we want to move to lightweight with all soft-syths. Our 140bpm tracks are too hard to play completely live, so a 2-octave keyboard is perfectly fine for playing a lead line, and the keyboard has these great touch pads for triggering samples. We like triggering samples, see the latest video on our facebook page.
We've been setting up our perfect performance environment on a laptop, using Fedora 13 as the base OS, but with a real-time kernel and some prebuilt packages from the Planet CCRMA repository.
Tracy wasn't sure if the keyboard was going to work okay in Linux and didn't find any useful information with Google, even looking for it's USB ID (09e8:0072). Fortunately the Akai MPK-25 is class compliant and works perfectly with Fedora 13 without needing to configure or install anything at all. It's even happy to be powered from just the laptop USB port cutting down on cables and adaptors.
$ aconnect -i
client 0: 'System' [type=kernel]
0 'Timer '
1 'Announce '
client 14: 'Midi Through' [type=kernel]
0 'Midi Through Port-0'
client 16: 'Akai MPK25' [type=kernel]
0 'Akai MPK25 MIDI 1'
1 'Akai MPK25 MIDI 2'
2 'Akai MPK25 MIDI 3'
$ aconnect -o
client 14: 'Midi Through' [type=kernel]
0 'Midi Through Port-0'
client 16: 'Akai MPK25' [type=kernel]
0 'Akai MPK25 MIDI 1'
1 'Akai MPK25 MIDI 2'
When using USB, the midi in and out connectors on the back become extra interfaces you can use too, those extra ports you can see shown above -- so we can have another keyboard and a sound module connected through the Akai to the laptop and save a midi interface.
I'll cover the software we're using for our live gigs in a later article; aside from the actual synth VST modules we use all open source.
It came as no surprise when Microsoft admitted to quiet security patching. We knew many years ago that they did this: not counting extra vulnerabilities that were found internally or by researchers contracted to work for them. For closed source, single vendor software, this isn't too big of a deal - it's not like the user has a choice if they need to update some application to address one critical vulnerability or 20.
When you look back, before they admitted to this practice, Microsoft actively used vulnerability counts in reports as a tool to discredit the security of open source distributions. Famously even Steve Ballmer participated in counting vulnerabilities using candy.
In other news, the Red Hat Enterprise Linux 4 risk report we release each year has been published (PDF). This whitepaper looks at the state of security for the first five years of Red Hat Enterprise Linux 4 from its release on February 15th, 2005. It includes metrics, key vulnerabilities, and the most common ways users were affected by security issues.
"Red Hat knew about 52% of the security vulnerabilities that we fixed in advance of them being publicly disclosed. The average time between Red Hat knowing about an issue and it being made public was 22 days (median 10 days).... A default installation of Red Hat Enterprise Linux 4 AS was vulnerable to 14 critical security issues over the entire five years. "
Red Hat Enterprise Linux 5.5 was released at the end of March 2010, just under 7 months since the release of 5.4 in September 2009. So let's use this opportunity to take a quick look back over the vulnerabilities and security updates we've made in that time, specifically for Red Hat Enterprise Linux 5 Server.
Errata count
The chart below illustrates the total number of security updates issued for Red Hat Enterprise Linux 5 Server if you had installed 5.4, up to and including the 5.5 release, broken down by severity. I've split it into two columns, one for the packages you'd get if you did a default install, and the other if you installed every single package (which is unlikely as it would involve a bit of manual effort to select every one). For a given installation, the number of package updates and vulnerabilities that affected you will depend on exactly what you have installed or removed.
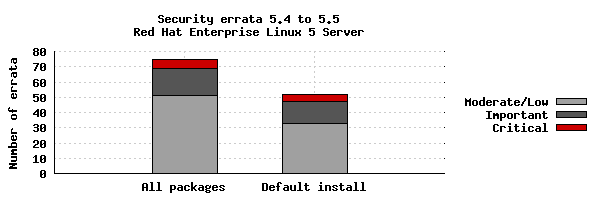
So for a default install, from release of 5.4 up to and including 5.5, we shipped 52 advisories to address 140 vulnerabilities. 5 advisories were rated critical, 14 were important, and the remaining 33 were moderate and low.
Or, for all packages, from release of 5.4 to and including 5.5, we shipped 75 advisories to address 187 vulnerabilities. 6 advisories were rated critical, 18 were important, and the remaining 51 were moderate and low.
Critical vulnerabilities
The 6 critical advisories were for 3 different packages. Given the nature of the flaws, ExecShield protections in RHEL5 should make exploiting the memory flaws harder.
- Four updates to Firefox (September 2009, October 2009, December 2009, February 2010) where a malicious web site could potentially run arbitrary code as the user running Firefox.
- An update to kdelibs (November 2009), where a malicious web site could potentially run arbitrary code as the user running the Konqueror browser. kdelibs is not a default installation package.
- An update to krb5, the Kerberos network authentication system (January 2010), where a remote KDC client could cause a crash or run arbitrary code as root. This issue only affected users that have configured and enabled krb5.
Updates to correct 24 out of the 25 critical vulnerabilities were available via Red Hat Network either the same day, or up to one calendar day after the issues were public. The update to fix Konqueror took us 4 calendar days.
Overall, for Red Hat Enterprise Linux 5 since release to date, 98% of critical vulnerabilities have had an update available to address them available from the Red Hat Network either the same day or the next calendar day after the issue was public.
Other significant vulnerabilities
Red Hat Enterprise Linux since 5.2 contained backported patches from the upstream Linux kernel to add the ability to restrict unprivileged mapping of low memory, designed to mitigate NULL pointer dereference flaws. In the last risk report we mentioned it was found that this protection was not sufficient, as a system with SELinux enabled was more permissive in allowing local users in the unconfined_t domain to map low memory areas even if the mmap_min_addr restriction is enabled. This is CVE-2009-2695 and was addressed in a kernel update in November 2009.
Previous updates
To compare these statistics with previous update releases we need to take into account that the time between each update is different. So looking at a default installation and calculating the number of advisories per month gives the results illustrated by the following chart:

This data is interesting to get a feel for the risk of running Enterprise Linux 5 Server, but isn't really useful for comparisons with other versions, distributions, or operating systems -- for example, a default install of Red Hat Enterprise Linux 4AS did not include Firefox, but 5 Server does. You can use our public security measurement data and tools, and run your own custom metrics for any given Red Hat product, package set, timescales, and severity range of interest.
See also: 5.3 to 5.4, 5.2 to 5.3, 5.1 to 5.2, and 5.0 to 5.1 risk reports.

